Sophos XG Firewall – The Complete Build and Maintenance Guide | Basic
This
guide is intended for network administrators aiming to deploy a Sophos XG
firewall device in an on-premise network environment. To ensure familiarity
with the device interface, the first section of the document will be dedicated
to an overview of all components of Sophos XG firewall.
Since
the device is expensive, costing about £2,000 for on-prem and £4,000 for the
cloud offering, Sophos have made available an online live demo which you can
register to use for practice;
Logging
into the portal should bring you straight into the Control Center interface as
shown below:
The
device serial number can be found at top left right below Control Center, along
with system metrics like performance, interfaces, system resource usage, high
availability configuration status and the total up-time of the firewall.
The
left pane of the interface offers all the configurable options available to
your XG firewall split into categories below:
Monitor & Analyse
Control Center
Current Activities
Reports
Diagnostics
Protect
Firewall
Intrusion Prevention
Web
Applications
Wireless
Email
Web Server
Advanced Threat
Central Synchronization
Configure
VPN
Network
Routing
Authentication
System Services
System
Profiles
Hosts and Services
Administration
Backup & Firmware
Certificates
Access Monitor&Analyze > Current Activities to reveal all live users and remote users. An administrator can disconnect any user whose machine may be posing a threat to the network.
Sophos XG offers a very detailed comprehensive
report statistics on the performance and state of your firewall. Navigate the
tabs to find information displayed in easy to analyse pie charts about Network
and threats, VPN, Email and Compliance.
Diagnostics tab offers a whole host of tools
for the Sophos XG firewall. You can perform packet capture analysis, manage
connection list and grant access to Sophos support for a set duration of time
to access the device. More details will be explored as this guide progresses.
Sophos
XG Registration & Set-Up
Now that we have explored the interface of the
Sophos XG firewall, we can now proceed to register and set up our device. We
shall explore 5 topics into detail regarding getting your XG firewall
operational;
1. Creating a Sophos ID
2. Start up and Registration
3. Completing set up wizard
4. Confirming your firewall is operational
5. Verifying & Synchronizing Licenses
Creating a Sophos ID
Fill in the name and business email and confirm
you are not a robot and register and account.
Confirm your email address with the link. You
want to check your junk mail folder if you haven’t received the message in a
while.
Set a very strong password and log into your
account with the new Sophos ID.
You may want to fill in the backup email and
phone information in the event you need to recover your Sophos ID account.
Once the backup information is completed and
saved, access My Applications > MySophos where you can select My Profile.
Fill in the information about the company you are setting up the Sophos XG
firewall.
Be sure to save all your changes after completing your profile and the
creation of your Sophos ID.
Start-Up and Registration
Before we begin setting up and registering our
firewall, there are some pre-requisites pictured below;
A Sophos ID which we created in our previous
step will be required, along with details of your internet connection from an
ISP containing the following information:
-Usable public IP addresses
-Subnet mask
-DNS server information
You can also visit Sophos.com/get-started-xg to
download the latest set up guide information about XG.
Assemble your XG Firewall and your WAN to Port
2 and LAN to Port 1 as pictured below:
If you have a laptop connected to port 1 and
have DHCP enabled, the laptop should pick up an IP address in range of the
Sophos XG device and you can log into the interface with IP 172.16.16.16:4444
Alternatively, you can hard code an IP address
in range on your network card. Eg. 172.16.16.2 which should put your Sophos
device and laptop on the same subnet.
Log into the XG interface with default
credentials admin/admin and accept the end user licenses and terms and
conditions associated with the use of Sophos XG firewalls.
We can now proceed with device registration by
clicking Basic Setup
Using the details provided by your ISP,
populate the public IP, subnet mask, default gateway and DNS information and
click save changes. Give the device about 30 seconds to initialize the network
config.
You will know the network update is successful
with a confirmation green tick pop-up. The device is now ready for Registration
by clicking the button and checking if its able to access the internet. If you
get an error at this stage, you may want to double check your settings from
ISP. [Use Sophos ID credentials].
The registration process may take a while, so
once complete you can proceed to synchronize your license with Sophos.
Completing Set-Up Wizard
Although this step may be skipped, it is
advisable to run the set-up wizard for the first time to ensure the necessary
modules and services are activated and verified. System configurations can
always be modified manually after the device is fully operational.
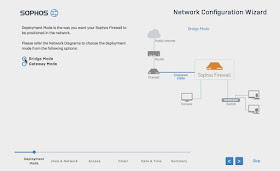
Two deployment modes exist for Sophos XG, Bridge Mode and Gateway
Mode
Bridge mode is used when there is an existing
firewall on premises, and you connect your Sophos device to port 2(WAN) using a
crossover cable. The firewall will then acquire its WAN IP via DHCP.
Gateway mode is used when the Sophos is
directly connected to the modem/router of the ISP on port 2 WAN with Port 1 LAN
connected to the switch on premises.
The most common option used is Gateway Mode
which should take you to the next step configuring your network interfaces.
Select a port, assign an IP address and mask and select the zone you want the
port assigned to. Eg. LAN, WAN, DMZ etc.
If you set your device to pick up DHCP
automatically, the details should be found on this page. You can input manual
DNS settings like Google 8.8.8.8 or CloudFlare 1.1.1.1 Host name will be your
Sophos XG serial number which should already be populated. You can add a
description if preferred.
The next step takes you to default network
policy settings. Tick User/Network Rule and recommended to leave Web Filter,
App Filter and IPS as None.
Network policies essentially lets an
administrator set LAN – WAN traffic rules for web filtering, app filtering and
Intrusion Prevention Systems. Traffic can be denied to all, allowed to all,
blocked for explicit content and advertising content.
More tools are available to configure these
rules to best suit the scenario of the production network.
If you have an email server, the details can be
populated here for system notifications. This setting can be edited later in
the configuration tools.
The last step is to set the time zones, date
and time for your XG device. You can tick the box to synchronize with NTP
Server.
Double check all the settings on the overview
windows and Click Finish to exit the config wizard.
A warning is likely to flash prompting the
wizard will flush all current settings. Since this is our initial set-up, you
can click OK to save the new settings.
The XG device should then reboot to configure
the mode of operation for the firewall.
Confirming your Firewall is Operational
Once the XG has booted up, you can log in with the default credentials Admin/Admin for the console.
In control centre, Click on Interfaces to
inspect the status of the LAN and WAN configurations we performed in the set-up
wizard.
Like the image above, you should see the status
of all your ports on the XG including LAN, WAN, Wireless and other unassigned
ports.
From there, click on Firewall and inspect the
rules set from the wizard are still present. The config will allow traffic from
any host on the LAN to the wider internet on the WAN.
Confirm everything is working by visiting your
favourite sites like google.com or Sophos.com
To confirm the connection status, access
Network and inspect the ISP settings configured in the set-up wizard is active
and connected. Check your ISP and DNS settings if you struggle to access the
external internet domains like Google.com
Verifying & Synchronizing License
Now the Sophos XG is set up and operational, we
can verify and synchronize our device with Sophos licensing portal.
This can be done in two ways; Access the
Administration > Licencing tab or click directly on the Administration tab
on the left main menu.
This interface displays all registration
information as well as module subscription details subscribed to. Click in
Synchronize to effect any changes.
You can check the expiry dates of added module
subscriptions like Network Protection, Email Protection and Email Protection.
Activating New Subscription Package
Depending on the requirements of the company, a
network administrator may need to install other modules such as Webserver
Protection or Sandstorm.
Any required modules will need to be purchased
from Sophos with license issues in a .pdf document like the sample below:
This document displays information about the
module purchased, the licence key and duration of the licence in months. Copy
this key and return to the licensing page on Sophos XG.
Click Activate Subscription and input the license key provided by Sophos
A pop-up window should appear where you can
paste and click Verify to validate and activate your new security package which
should show a status as Subscribed in Green when active.
Sophos XG Firmware Update and Roll-Back
This section of the tutorial will examine the status of the firmware
running the Sophos XG firewall, versioning and how to update as well as roll
back to a previous firmware version if things go wrong.
When an update becomes available, you would get
a prompt the next time you access the dashboard. You can proceed by clicking
the link, bearing in mind never to update anything without first backing up the
current configuration.
Alternatively, you can manually navigate to
System > Backup & Firmware to access the backup interface, API, firmware
and the ability to import or export a firewall configuration to file.
Only after you’ve taken a config backup, click
to download and install the new firmware bearing in mind a device reboot will
be required to complete the upgrade. Check the firmware version when the system
boots back online.
Some situations may arise that sees the XG
firewall offline and unable to automatically download firmware updates. Using
your Sophos ID account, you can access the firmware
Your device serial number will be required to
locate the correct firmware, which can be found on your Sophos XG dashboard.
Once your firmware is located, download it to
your PC and upload it via the upload firmware tab below the exiting active
firmware running on the firewall. Give it a few minutes for upgrade and reboot.
Whenever a firmware update is performed on the
Sophos XG, the system preserves the previous firmware in the event a roll back
is required. Navigate to Systems > Administration > Firmware and notice
both old and new firmware images are available in the tab.
To roll back to previous version, simply click
on Boot firmware image and OK to roll back the XG device.
Bear in mind any configuration
changes made to the device will be lost when firmware is rolled back.
Sophos XG Administrator Password and Device
Access
In this section we shall examine the
administrator password, how to change it and manage access to the Sophos XG
device.
When you log into your dashboard, you will
notice an alert highly recommending the Admin password be changed. Click on the
link or navigate to Systems > Administration > Device Access.
If more specific rules are required such as
limiting SSH access to only Admin computers, click to edit and fine tune ACL
exception rules to your network specifications.
Remember to save any changes made to
the device access control list.
It is recommended to set a very complex and
strong password combination, preferably with lower case, upper case, numbers
and symbols to ensure the device cannot be breached using brute force attacks
or password dictionary attack methods.
Sophos XG Using Captive Portal for
Authentication
This section will examine how we can use
captive portal on the XG firewall for authentication.
Why Use Active Portal?
-You can have firewall access rules that
require authentication to access the internet or various network resources.
-If a user fails to access the internet or
network resources using SSO, NTLM, Radius or Guest Services, Captive Portal can
be used to authenticate the user and gain access to those resources.
-Captive Portal serves as a last resort for
authenticating with the firewall.
When Using Captive Portal for Internet Access
-An unknown user trying to access the internet
should be redirected to the Captive Portal.
-On most networks, DNS settings are inherited
on the WAN port from the Internet Service Provider (ISP).
-When you are blocking WAN access for unknown
users, they cannot reach the DNS server that is out on the WAN.
-Therefore, a user trying to access the
internet where authentication is required, will not be redirected to the
Captive Portal.
-A separate firewall access rule is that does
not require authentication is needed for WAN DNS access.
WAN DNS Access Rule to be added:
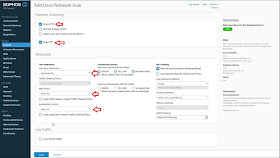
· Create a firewall rule
by clicking on “+Add Firewall Rule” in the upper right corner of the firewall
user admin interface Protect > Firewall with the following settings;
-Rule Name: Allow WAN DNS Access
-Description: Allows anyone access to
DNS servers located outside on the WAN port
-Action: Accept
-Source Zones: LAN
-Source Networks and Devices: Any
-Destination Zones: WAN
-Destination Networks: Any
-Services: DNS
-Match known users: Make sure this box
is UNCHECKED
-Click Save at the bottom of the screen
Configuring and Enabling a Captive Portal for
a Zone
Captive portal is a great access control tool
configurable on the Sophos XG firewall that enables network administrators to
control user’s access to the internet, by making users known to the firewall.
To access the interface, navigate to Configure
> Authentication > Captive Portal to display the General Settings.
The Sophos logo in the pop up can be changed to
a custom logo by clicking Custom and browsing for the new logo. You can use the
log URL to direct users to a specific page when they click the logo.
The Page Title, header and footer messages can
also be edited in the provided fields. The option to change the colour schemes
of the page can also be done at the bottom of the captive portal page.
Now we have configured the captive portal, lets
head back to System > Administration > Device Access and make sure the
Captive Portal on LAN is ticked > Apply and OK.
With the Captive Portal active, we can now
create a new firewall rule for users on the LAN zone to access the internet on
the WAN zone. Navigate to Protect > Firewall > Add Firewall Rule >
User/Network Rule on the IPv4 interface.
You can now populate the interface with the
firewall WAN access rules we set on page 26 with the name ‘Internet Access for
Known Users’. Set Rule Position to Top and remember to check ‘Show captive
portal to unknown users’ before clicking Save.
This rule configuration should then direct any
user who is not known to the XG firewall to the captive portal for
authentication, before allowing access to the internet.
Below the firewall rule settings can be found
Malware Scanning settings, tick ‘Scan HTTP’ and ‘Scan FTP’
In the advanced section set ‘Intrusion
Prevention’ – GeneralPolicy, ‘Web Policy’ – Allow All, ‘Application Control’ –
Allow All and tick ‘Log Firewall Traffic’ to ensure any users that redirected
to the captive portal is logged for analysis.
The firewall rule ‘Internet Access for Known
Users’ should now be visible on the dashboard with status turned on.
Since most networks are set to use external DNS
servers for name resolutions, and there is no DNS server on the network, users
who try to access the internet will not inherit DNS settings from the WAN port,
and therefore will not be directed to the captive portal.
To ensure users can gain access, we need to
create another rule to allow access to external DNS on the WAN interface.
The configuration is like the one above except
the services is set to DNS and ‘Match known users’ Unchecked.
To test the firewall rules you have set,
deactivate Allow WAN DNS access and notice a user will be unable to get out to
the wider internet. Turning it back on should now redirect the user to the
captive portal page, after a warning is displayed prompting an insecure site.
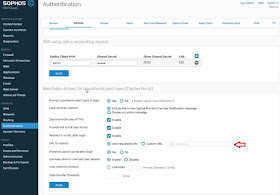
Customize the behaviour of the captive portal
by navigating to Configure > Authentication > Services and scroll down to
Web Policy Actions for Unauthenticated Users (Captive Portal)
You will find the ‘User request URL’ is ticked
by default so a user will be redirected to the page they have requested after
authenticating with the captive portal. Click ‘Custom URL’ to direct users to a
specific site such as a company website.
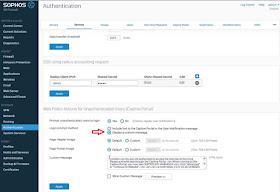
By default, the user notification message
includes a link to the Captive Portal. This can be changed by clicking on
‘Display a custom message’, which can be formatted in HTML. You have the option
to customize your company header and footer logos with images of size 700 x 80
Pixels.
Sophos XG Firewall Backup, Restore &
Factory Reset
Now that we are comfortable setting up the XG
firewall for internet and managing users in captive portal, this section will
elaborate on how to back up configuration of the device, restore and reset the
XG to factory settings in the event of a disaster.
Navigate Systems > Backup & Firmware to
access the interface where you can perform local, FTP or Email backups with
varying frequencies depending on the organizations’ security policies.
Remember that to use Email backup mode, you
will need to have set up the email in the notification screen from System >
Administration > Notification Settings.
Make sure to assign a prefix you can identify
if you work with or operate multiple XG firewalls in the environment.
Since the XG device can become inaccessible for
any reason, it is advised not to rely solely on local backups but send backup
files to email periodically.
The latest backup file can always be in this
interface with a timestamp of the file. Download and restore if the system
becomes inoperable.
Bear in mind that any configuration
made after backup files are restored, will be lost unless a new backup is
taken.
There are scenarios when the Sophos XG firewall
becomes inaccessible due to one of many factors. The device could lose power
during a firmware upgrade for example, rendering the Sophos OS corrupt.
Navigate to System > Backup & Firmware
> Firmware, click on the settings cog on the current firmware version >
Select Boot with factory default.
Bear in mind once the device is reset
to factory settings, all configurations will be lost. It is highly recommended
to have a backup of the current configuration before performing this operation.
Summary
This
completes the tutorials for basic configuration of Sophos XG Firewall. Further
study in intermediate configuration and advanced configurations are required
for network administrators to effectively manage a corporate network
infrastructure.
We would
like to thank you for investing your time with us.
Written By:
www.codexploitcybersecurity.com Reddit: /r/Codexploitcyber Facebook: https://www.facebook.com/icybersecure
Credits to all
organisations and development teams at Sophos Labs










































































0 Comments:
Post a Comment