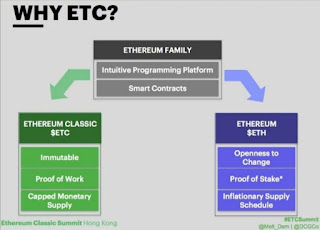
At this point, it’s worth noting the difference between Ethereum Classic ETC and Ethereum ETH which is a fork of ETC and therefore share the same algorithmic programming.
Ethereum Classic (ETC) is secured by Proof-of-Work algorithm, which makes ETC a Sovereign Grade Censorship Resistant Blockchain like Bitcoin, whiles Ethereum (ETH) uses a Proof-of-Stake* algorithm susceptible to interference from external forces including the risk of capture by malicious organizations.
Both are EVM compatible and Turing Complete, which enables them to execute Smart Contracts like the one that generated The Genesis Heist Comic NFTs.
Creating a MetaMask account does not require a user to provide their email address or phone number, just a 12-word seed phrase and a password which should be kept secure, not to be shared with anyone and ideally stored in multiple locations.
Follow the instructions to create a new account and record your 12-word seed phrase carefully.
2.Selecting a Blockchain Network
As a gateway to Web3, MetaMask allows you to connect to several Blockchains besides the default Ethereum network.
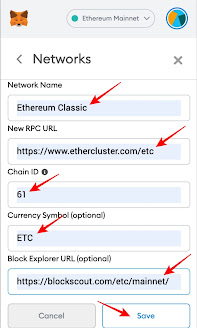
Ethereum Classic blockchain which runs the ZEUS COMIC smart contract shares similar charactristics to Ethereum, except operating a proof-of-work algorithm and different Remote Procedure Call RPC network settings to connect to the blockchain.
Network Name: Ethereum Classic
New RPC URL: https://etc.rivet.link
Chain ID:
61Currency Symbol (optional):
ETCBlock Explorer URL (optional): https://blockscout.com/etc/mainnet/
Once satisfied you have entered the details correctly, click “Save” and Add ETC network to MetaMask.
4.Connecting, Viewing and Managing Your New MetaMask ETC Wallet
Congratulations! You have now completed the process of configuring ETC network on MetaMask.
It is always advisable to test transactions with small amounts before moving a large amount of funds.
Minting or Buying The Genesis Heist Web3 Comic NFTs on Ethereum Classic ETC
Well done for coming this far, we are now ready to mint The Genesis Heist Web3 Comic NFT by accessing the mint page on the secure URL: https://www.thegenesisheist.app/
MetaMask will pop up a notification to approve your wallet to interact with The Genesis Heist Web3 Comic NFT Smart Contract, and then you can mint for 1 ETC The Genesis Heist Comic NFT on the Ethereum Classic ETC network.
Minting should complete after confirming gas fees on MetaMask and receive your Genesis Heist Comic NFT.
Click on Read Comic Book to open the comic reader program in your browser to reveal the flipbook Genesis Heist Comic book.
Why “The Genesis Heist” Is One of the Most Innovative Projects in Web3 Right Now
Most of us in the crypto community are deeply familiar with the need for real education around how Bitcoin and blockchain tech actually work. But let’s be honest — whitepapers, technical docs, and YouTube explainers can be dry, overwhelming, or just plain inaccessible to newcomers.
That’s where The Genesis Heist stands out.
🚀 A Comic Book That Teaches Bitcoin? Yes, Really.
The Genesis Heist is more than a comic — it’s an immersive, story-driven educational experience. Set in a vibrant, visually stunning world, the story revolves around themes of decentralization, power, and digital freedom. But underneath the rich narrative and bold artwork is something deeper:
✅ Grassroots education on proof-of-work technology
✅ Exploration of real-world Bitcoin use cases
✅ Hands-on exposure to wallet management and asset security
Through storytelling, it teaches people not just what Bitcoin is, but why it matters.
🧩 The Bitcoin Treasure Hunt: Learn by Doing
One of the most exciting parts of the project is the Bitcoin treasure hunt embedded within the story. Clues throughout the comic point readers to a real treasure — Bitcoin locked behind a puzzle.
To play, you’ll need to:
-
Understand Bitcoin wallet fundamentals
-
Navigate how UTXOs and private keys work
-
Practice real asset security principles
It’s a gamified, practical education that rewards curiosity and engagement — not just consumption.
Think of it as onboarding to the Bitcoin rabbit hole, but through a cyber-noir, high-stakes narrative that hooks you emotionally and intellectually.
🔍 Why It’s Innovative
Blending Art with Infrastructure: This isn’t just “blockchain for artists” — it’s art as infrastructure for onboarding. It builds emotional bridges to technical ideas.
Real Utility: Unlike so many NFT projects that are just speculative fluff, The Genesis Heist offers tangible learning outcomes.
Long-Term Vision: It plants seeds for a more informed, secure, and philosophically grounded next wave of crypto adopters.
Decentralized Distribution: By living on IPFS and embracing Web3-native formats, it preserves its mission of censorship resistance and open access.
🤝 Why the Community Should Support It
If you care about:
Wider adoption of Bitcoin and PoW tech
Onboarding new users the right way
Building community through storytellin
Investing in long-term value over hype
Then The Genesis Heist is exactly the kind of project we need to amplify.
It’s rare to see a project with this kind of vision, execution, and grassroots energy in the Web3 space — and it deserves the support of both the community and serious-minded investors.
Check it out at https://thegenesisheist.app and see for yourself why The Genesis Heist isn’t just a comic… it’s a movement.
Adding Your ZEUS COMIC NFT to Your MetaMask Wallet
After your comic is successfully minted, you can inspect the asset on BlockScout ETC explorer Zeus Comic Inventory
- ZEUS COMIC Contract Address:
0x26B24bE02620214995911a5123e964EF7A962a79
Locate your asset ID# in block explorer and make note of the number. If not already appeared click NFT tab in MetaMask and +Import NFT. Input the Zeus Comic contract address and your ID# to manually add the comic NFT assets to your wallet.